In a Nutshell
- Reverse proxy servers are important “gatekeepers” for many IT systems
- The proxy is the one and only point of contact for external requests
- A reverse proxy can increase the performance and security of an IT system
- There are numerous software solutions for implementation - depending on requirements
- Professional setup is essential
What is a Proxy Server?
A classic proxy server is a server that receives requests from multiple clients and forwards them to their destination. These can be websites, apps and other services. As a “forwarding proxy” or “switching proxy”, it takes over communication with the respective service and establishes a connection without the website being able to see which end device this connection originally came from.
This is often referred to as a forward proxy. Responses from the service are then forwarded to the proxy, which in turn returns them to the client. This means that the client remains completely anonymous to the website, application etc. during communication.
A reverse proxy is a physical / virtual server that receives incoming requests from clients and forwards them to connected servers. This reverse proxy server acts as a mediating control instance and makes it possible to control the load distribution in the system and to increase the security and performance of services and web applications.
Put simply, the reverse proxy is the counterpart to the forward proxy: it acts as an intermediary between client and server, but the actual server remains anonymous. The end user is unaware of this forwarding of their request - the reverse proxy is the only “point of contact” for the client.
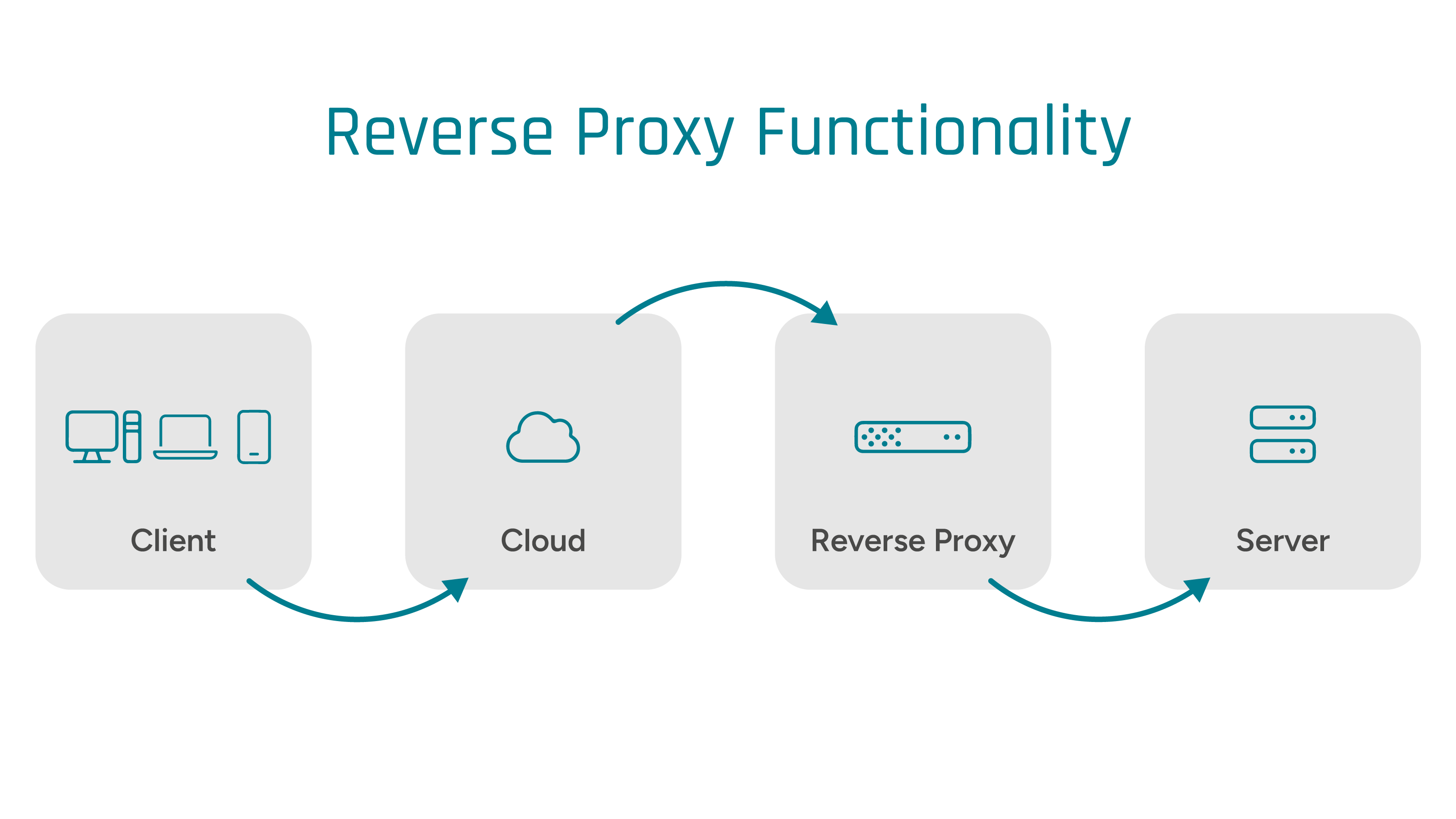
How a Reverse Proxy Works
Let's assume that a user wants to use a digital service from a company. To do this, they access the company's website from their cell phone (client), for example. If the company now uses a reverse proxy server, communication takes place as follows:
Request
As the reverse proxy is connected upstream of the website's web servers, the initial request is first sent to the proxy.
Forwarding
Depending on the configuration, the server then checks the request for possible security risks. The request is then forwarded to one of the linked web servers.
Response
According to the request, the web server delivers the requested information to the reverse proxy. This forwards it to the user's client, which concludes the communication. The IP address of the web server remains completely secret.
At first glance, this intermediate step via a proxy seems quite trivial. However, such a setup actually offers companies enormous opportunities in terms of the protection, performance and scalability of their own web services.
Advantages of a Reverse Proxy
The use of a reverse proxy offers the following advantages:
Load Balancing / Load Distribution
A reverse proxy is very often used for load balancing. It distributes incoming requests as evenly as possible across the linked server pool according to specific specifications. This load balancing allows both the resources of your own server IT to be used efficiently and large volumes of requests to be processed at once.
If a server fails, the traffic is simply redirected to an alternative server by the reverse proxy. And if the company or IT grows, the pool is simply supplemented with additional servers that the proxy can control in its function as a load balancer.
Server Security
As external clients only communicate with the reverse proxy server and the IP of the web servers always remains anonymous, attackers find it difficult to target them. By using conventional firewalls and advanced web application firewalls (WAF), even encrypted data traffic can be checked for malicious content.
The check helps to defend against attacks with malicious SQL code (SQL injection) or cross-site scripting (XSS), for example.
Caching / Compression
In order to answer frequently recurring requests more quickly, the corresponding information / files can be stored in the local memory (cache) of the proxy server and retrieved from there. In this way, requests are answered directly without the reverse proxy having to contact the web servers again. This shortens response times and at the same time conserves the resources of the linked web servers.
At the same time, reverse proxy servers offer the option of compressing content such as pages, files or scripts before responding to the client. This reduces the size of the data packets, improves the loading time, especially with a poor Internet connection, and also reduces the overall utilization of the network.
SSL/TLS Termination
Encrypted requests must first be decrypted before they can be processed, which requires computing power. Using SSL offloading or SSL/TLS termination, the reverse proxy server decrypts the incoming data traffic before the requests are forwarded to the web servers.
The proxy server also re-encrypts the responses before they are sent to the user client. This eliminates the entire overhead for the web servers for decrypting/encrypting all requests and responses, which contributes to the efficient use of available resources.
Request a callback
Areas of Application and Use Cases
Due to the various functions that a reverse proxy can fulfill in addition to the pure forwarding of client-side requests, this technology is used in numerous IT infrastructures today. These intermediaries can be found particularly frequently in the following scenarios.
Cloud Applications
For cloud-based services, reverse proxy servers offer the advantage of particularly easy scalability. For example, if a specific service is in high demand, additional servers can be provided with minimal effort and coordinated at a central location - the reverse proxy. At the same time, the proxy ensures low latency and short response times for a consistently good user experience - essential for the provision of Software-as-a-Service (SaaS) solutions, for example.
Corporate Networks
A reverse proxy can be used to protect your own company network from unauthorized access. For example, access to the entire network or specific sub-areas can be controlled. This applies to both company-owned clients such as work laptops and private devices, as the proxy fulfills its function independently of the client.
CDNs (Content Delivery Networks)
Reverse proxy servers are often used in conjunction with (global) content delivery networks. These are essential, particularly in the area of e-commerce or streaming, in order to ensure the rapid provision of content worldwide. In particular, caching and the ability to compress data packets enable fast, reliable and secure delivery of content/media of all kinds.
Reverse Proxy / Load Balancer / API Gateway - Working Together for the Security of Your IT
The terms reverse proxy, load balancer and API gateway are closely linked. These technologies are often used in combination in modern IT infrastructures to efficiently control data traffic, scale applications and meet security requirements. This is particularly true for complex IT environments such as cloud architectures. The collaboration between the technologies can look like this:
Checking Requests by Reverse Proxy:
Incoming requests in the system are received by the reverse proxy server. The requests are decrypted using SSL/TLS termination and unwanted or malicious requests are already blocked at this point. In this way, all resources are focused on responding to legitimate requests.
Load Distribution through Load Balancers:
Next, a load balancer takes over the requests and distributes them to the connected servers according to a defined algorithm. This ensures that the available resources are used efficiently and that performance is consistently good.
API Management with API Gateway:
An API gateway handles API requests separately. Such gateways are used particularly frequently in the management of microservices (user management / payment processing). Similar to a load balancer, they then forward the requests accordingly. At the same time, the gateway also performs central functions such as monitoring, authentication and authorization of all API accesses.
Reverse Proxy - Challenges in Practice
The opportunities that technologies such as proxy servers offer companies are obviously manifold. However, there are a number of challenges that need to be kept in mind in order to make optimum use of them.
Complex Setup
The initial setup of a reverse proxy server can be quite complex, depending on the technology and the given IT environment. However, incorrect setup can result in high latency times or critical security problems. Proper server setup is therefore absolutely essential.
Single Point of Failure
When using a reverse proxy, companies should make absolutely sure that redundancies are in place or failover mechanisms are set up. Otherwise, the failure of the proxy can significantly impair the processing of all data traffic.
Regular Updates
The gatekeeper function gives the proxy a vital protective function - provided that virus signatures are up-to-date and regular updates are carried out. It is precisely at this IT interface that companies cannot and must not allow themselves any vulnerabilities.
Request a consultation
